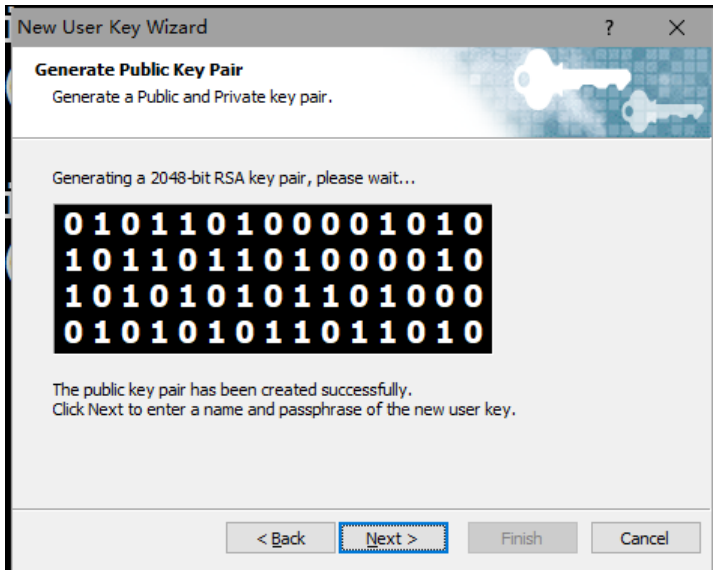
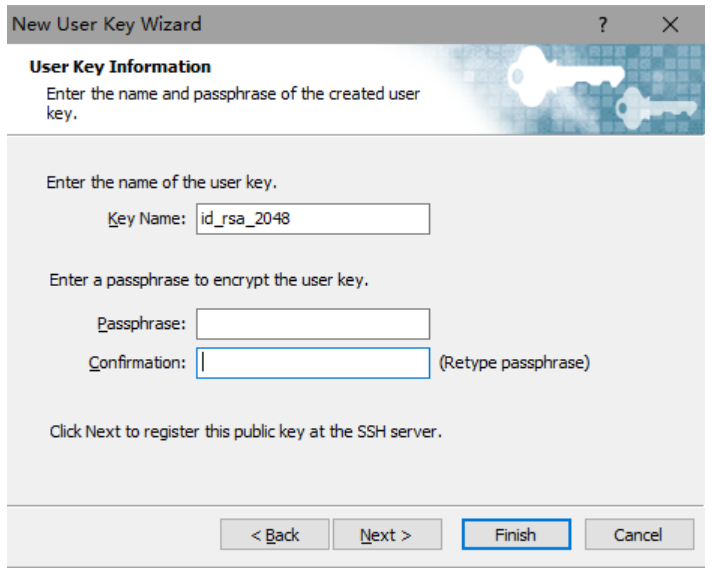
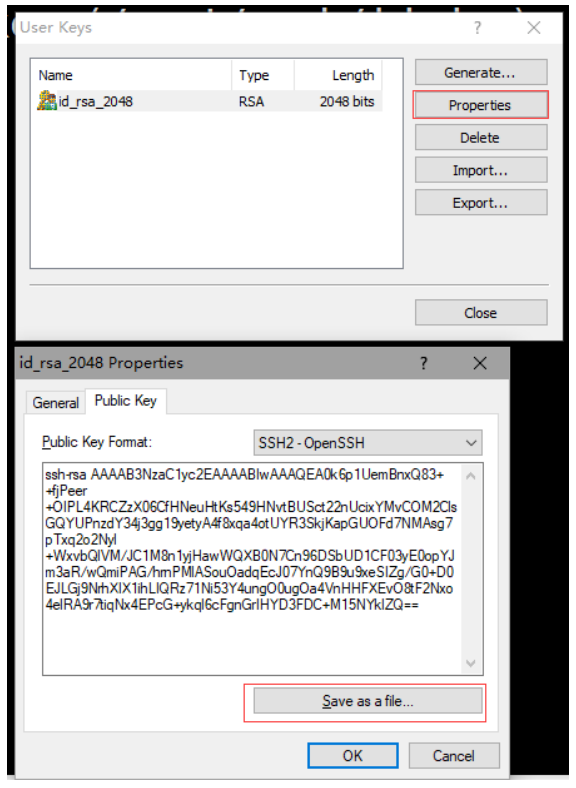
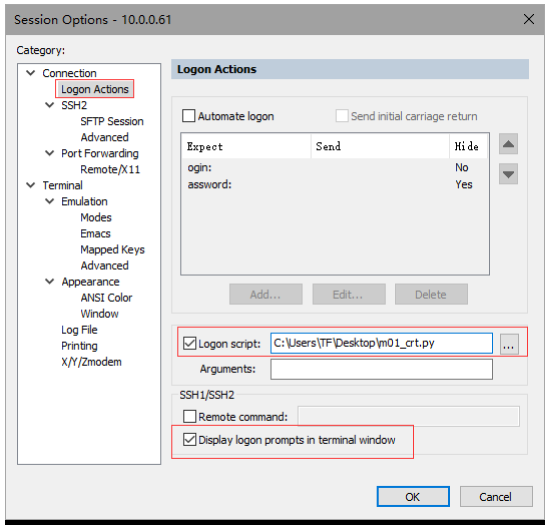
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
|
import hmac, base64, struct, hashlib, time,re
objTab = crt.GetScriptTab()
objTab.Screen.Synchronous = True
objTab.Screen.IgnoreEscape = True
tabName=objTab.Caption
reIp=r'\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3}'
hostIp=re.findall(reIp,tabName)[0]
secretKey="Your new secret key is:"
def calGoogleCode(secretKey):
t = int(time.time())//30
lens = len(secretKey)
lenx = 8 - (lens % 4 if lens % 4 else 4)
secretKey += lenx * '='
key = base64.b32decode(secretKey)
msg = struct.pack(">Q", t)
googleCode = hmac.new(key, msg, hashlib.sha1).digest()
o = ord(str(googleCode[19])) & 15
googleCode = str((struct.unpack(">I", googleCode[o:o+4])[0] & 0x7fffffff) % 1000000)
return googleCode.zfill(6)
def get_string(objTab,szStart,szPrompt):
objTab.Screen.WaitForStrings(szStart)
return objTab.Screen.ReadString(szPrompt)
def send_string(objTab,waitString,strings,selfSleepTime=20):
objTab.Screen.WaitForStrings(waitString)
time.sleep(0.0001)
for i in strings:
crt.Sleep(5)
objTab.Screen.Send(i)
objTab.Screen.WaitForStrings(strings)
if strings[-1] != '\r':
objTab.Screen.Send('\r')
def send_pass(objTab,waitString,strings):
objTab.Screen.WaitForStrings(waitString)
for i in strings:
crt.Sleep(5)
objTab.Screen.Send(i)
if strings[-1] != '\r':
objTab.Screen.Send('\r')
time.sleep(0.01)
send_pass(objTab,'Verification code:',calGoogleCode(secretKey))
send_pass(objTab,'Password: ','1')
send_string(objTab,'Opt> ',hostIp)
|